This series “Digital security” is from my notes prepared for certifications.
Certificates are linked to “Identity” by leveraging the security of digital signatures(asymmetric key cryptography and hash functions).
A certificate has following information:
- Subject’s name and public key (Who the certificate is issued to)
- Issuer’s name and signature (Who issued the certificate)
If the issuer and subject are the same entity, the certificate is considered to be self-signed. These are good for development or internal/local uses where secure applications require certificates within the network.
Over the internet, there are security firms that issue certificates. These are often called the Root Certification Authority (Root CA).
The Root CA don’t directly sign all the domain/server/vanity certificates. The Root CA create multiple intermediate CA who then sign the end user certificates.
This mechanism of chained trust to authenticate a host/client over the network is known as Public Key Infrastructure(PKI).
Web browsers by default, have a certificate store which contains the certificates of many Root CA and intermediate CA.
In addition to browsers, application servers (IIS, Tomcat, NGINX, etc) have their own collection of certificates to trust incoming client or outgoing server connections.
In addition to these specialized applications (Browsers and App servers), the operating systems has its own certificate store used by client applications (Skype, Office, 7Zip, Fiddler, Postman, etc).
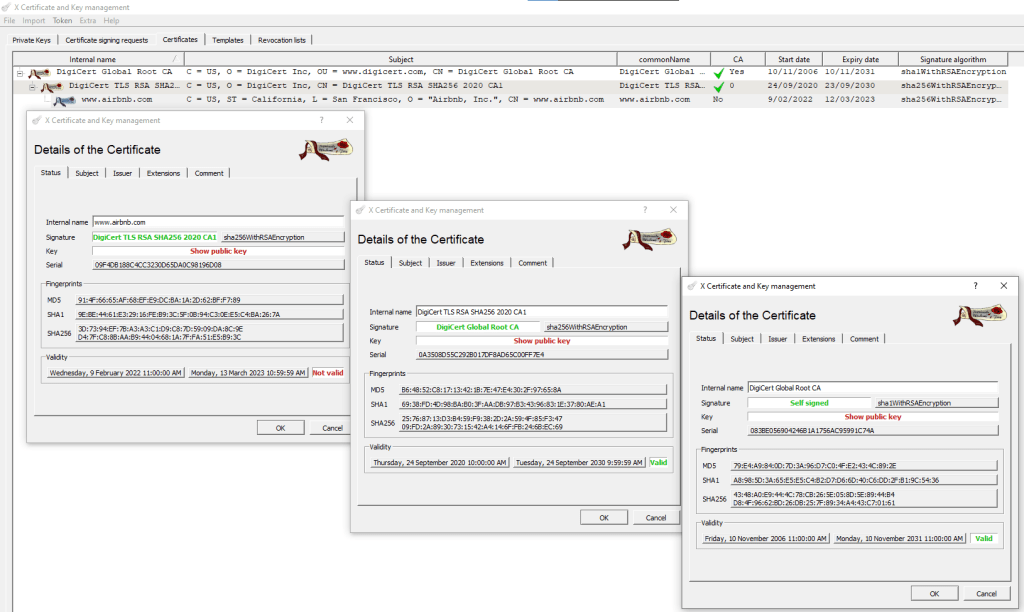
Inspecting a certificate will show that the certificate was most likely issued by an intermediate “Issuing Authority”. Below screenshot was taken by importing certificate of www.airbnb.com and all certificates in its chain of trust.
The certificates were analysed on 28/03/2023. The end user certificate had expired at this point.
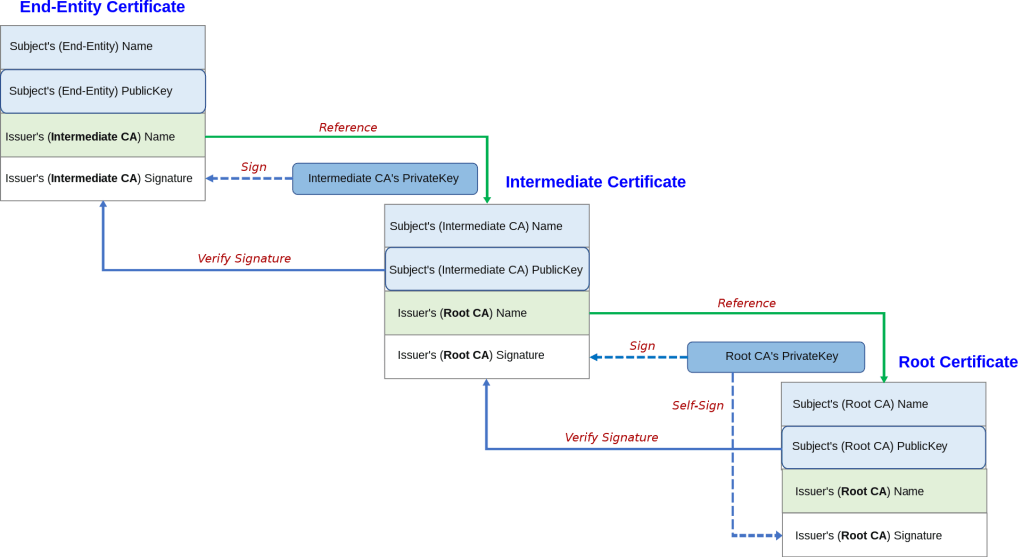
The Root CA’s public key is hashed and that hash is encrypted using Root CA’s private key. This results in the Root CA’s signature.
The Root CA’s public key and signature are then shared to the public. Anyone who wants to validate the public key and also authenticate the sender, can verify the signature.
Root CA’s self signed certificate contains Root CA’s public key and Root CA’s signature.
Root CA’s signature is then attached on Intermediate CA’s certificate, along with Intermediate CA’s public key. Intermediate CA generates its own signature using its public and private keys.
End user’s certificate will contain Intermediate CA’s signature, end user’s public key.
To validate end user’s certificate, we validate the end user signature using the end user certificate’s public key. This leads us to validate Intermediate CA’s signature.
The browser/web-server/OS might have Intermediate CA’s public key which can be used to validate that Intermediate CA’s signature. This leads us to validate the Root CA’s signature.
The Root CA’s public key SHOULD BE available at the client’s browser/web-server/OS in order to validate the Root CA’s signature.
The chain of trust will stop there because Root CA’s certificate is self-signed.
Below image from wikipedia:
Digital signature, Certificates, SSL/TLS are a layer 4+ mechanism to ensure confidentiality, integrity and authentication.